Control contractor &
vendor access
Grant temporary, monitored access to external collaborators without exposing core systems. Time-limited credentials, granular permissions, and complete audit trails.
Proactive protection for
privileged accounts

Privileged Access Management
Admin Console Preview
You trust your privileged users with elevated access to critical systems, data and functions. But that advanced entitlement needs to be verified, monitored and analyzed to protect your resources from cybersecurity threats and credential abuse. Research has found that as much as 60% of insider cyberattacks involved privileged users.
valtrogen access control enables zero trust strategies to help minimize risk to the enterprise.
Benefits
Manage privileged accounts
Discover unknown accounts. Reset passwords automatically. Monitor anomalous activity. Manage, protect and audit privileged accounts across their lifecycles.
Enforce endpoint security
Identify devices, servers and other endpoints with administrator privileges to enforce privilege security, control application rights and reduce the impact on support teams.
Protect DevOps secrets
Centralize secrets management, enforce access and generate automated legged trails with high-velocity, platform-neutral vaulting.
The cost of
uncontrolled access
Read the full report287
days average time to identify and contain a breach caused by compromised credentials.
$4.5M
average cost of a data breach involving third-party access in 2024.
Features
Dashboard
Manage API keys, credentials, certificates and more within one rich UI. Auto-rotation and access control.
Secrets groups
Manage access policies at enterprise scale. Group contractors by project, department, or access level.
Notifications
Configure with Event Notifications Service to receive secrets life-cycle events in real-time.
Locks
Create locks on secrets to prevent them from being deleted or modified while in use.
Certificate Management
Use the imported certificate type to create private keys and CSRs, and manage all your secrets in one secure, dedicated space.
Custom credentials
A customizable set of parameters that define how a secret interacts with a credentials provider.
What's your contractor
use case?
Password vaulting
Securely store and manage contractor credentials. Auto-rotate passwords without sharing them directly.
Our platform integrates with your existing tools to provide security where teams manage secrets. Its secrets group feature and activity tracker ensure proper access control.
Explore contractor management
Who benefits from
controlled access
Development teams
95%
faster onboarding
External developers access staging environments instantly. No IT tickets, no waiting.
Read moreCompliance officers
Full
audit coverage
Complete logs of all contractor activity. Ready for any compliance review.
Read moreSecurity teams
No
shared credentials
Every contractor gets unique credentials. Revoke access quickly.
Read moreComplete access control
Contractor access is just one part of a comprehensive security strategy. Explore related capabilities.

Team member management
Centralized control for your internal team. Same platform, unified billing.
Learn more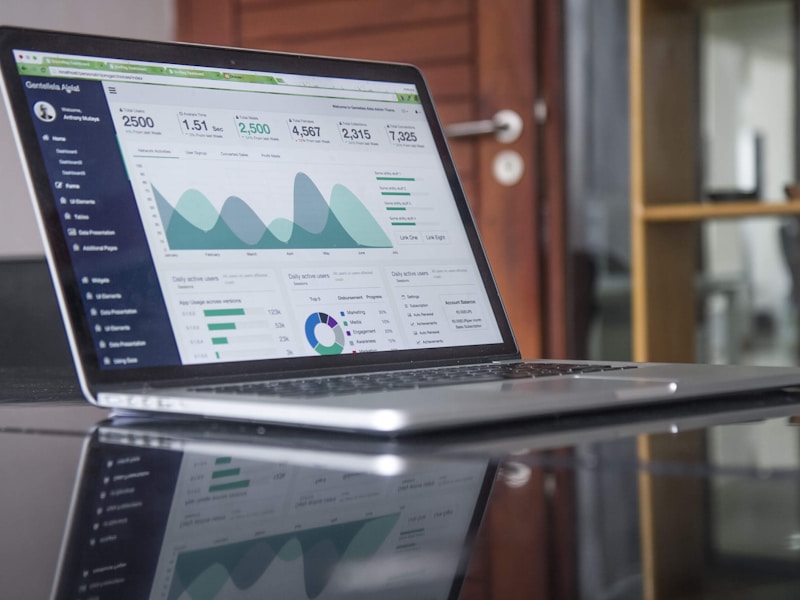
Usage analytics
Real-time visibility into who's using what. Identify patterns and optimize costs.
Learn more
Security policies
Define organization-wide rules. Apply consistently across all users.
Learn more
Compliance exports
Generate reports for auditors. Prove compliance with detailed logs.
Learn moreTake the next step
Talk to our team to get started with contractor access control today.
More ways to explore
FAQ
Instantly. Create credentials in the admin console, set permissions and expiration, and share via email. The contractor can connect within minutes.
Yes. You define exactly which internal resources are accessible through the contractor's connection. Everything else remains invisible and unreachable.
Credentials automatically stop working. The contractor cannot connect, and any active sessions are terminated. No manual intervention required.
Yes. The admin console shows real-time connection status and provides detailed logs of all activity. You can export these for compliance or incident investigation.
Contractors use your team's shared traffic pool. You can set individual usage limits per contractor to control costs and prevent abuse.